雲端式保護措施
透過集合功能整理內容
你可以依據偏好儲存及分類內容。
分析與查看
應用程式在 Google Play 提供下載之前,我們會分析及審查應用程式和開發人員。我們會努力運用自動偵測機制 (例如機器學習) 和人工審查員,確保 Google Play 中顯示的應用程式不會對使用者或其裝置造成傷害。
開發人員審查
開發人員必須同意《Google Play 開發人員發行協議》,才能將應用程式提交至 Google Play。
這份合約旨在說明開發人員在 Google Play 發布應用程式時應遵守的行為。
此外,Google Play 會使用各種方法檢查開發人員是否遵守這些政策。Google Play 的內部風險引擎會分析開發人員 Google 帳戶、動作、記錄、帳單詳細資料、裝置資訊等資訊。如果發現可疑項目,我們會手動審查交易,確保開發人員遵循相關法規。
內部應用程式審查
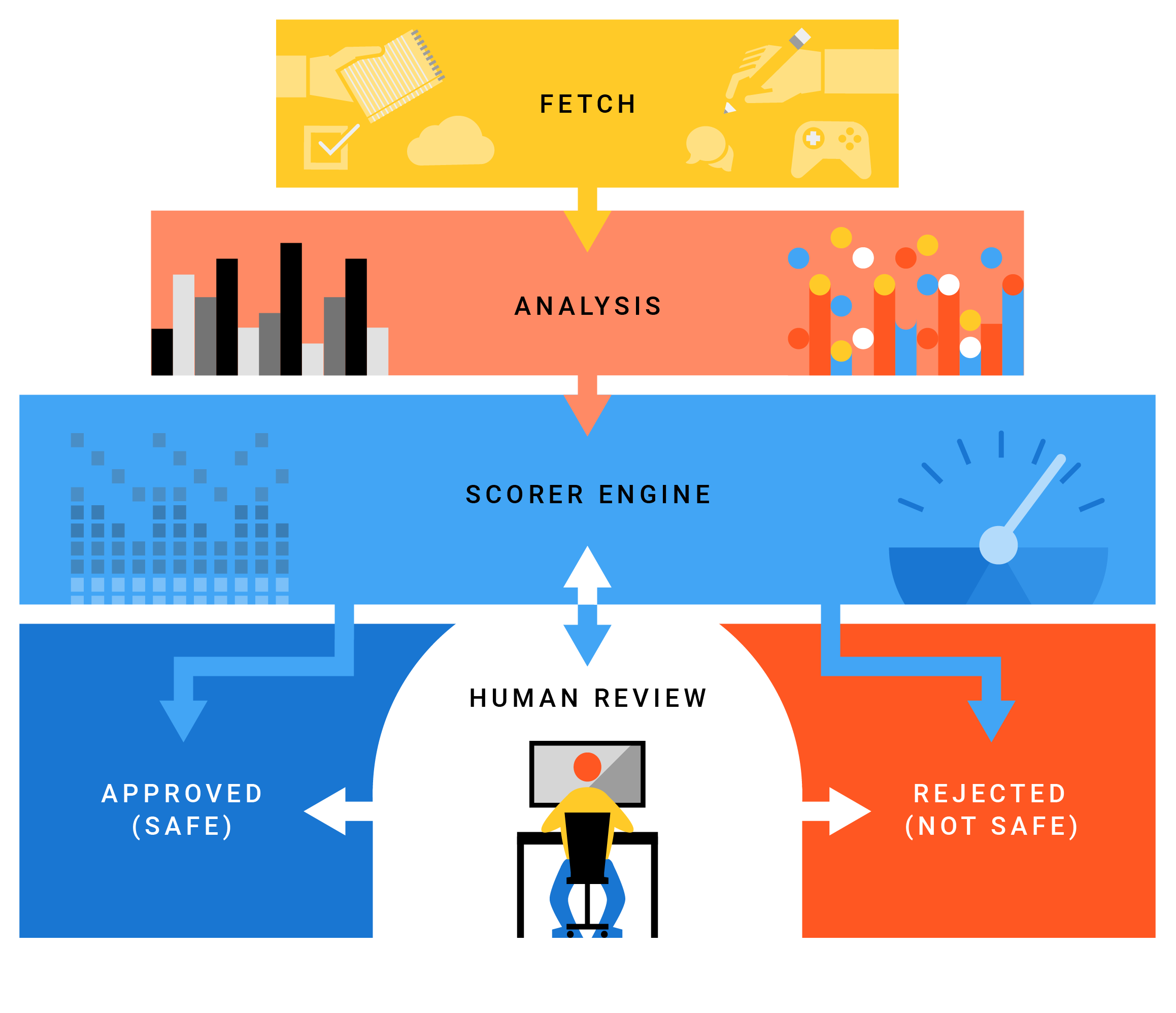
應用程式會經過審查,確認符合 Google Play 政策規定,才會在 Google Play 上架。Google 開發了自動化的應用程式風險分析工具,可對應用程式執行靜態和動態分析,藉此偵測可能有害的應用程式 (PHA) 行為。如果 Google 的應用程式風險分析器發現可疑內容,就會標記該應用程式,並交由安全性分析師進行人工審查。
Google Play 以外的應用程式審查
我們嘗試保護使用者不受 PHA 和行動垃圾軟體 (MUwS) 的侵擾,無論來源為何,我們的系統都必須盡可能分析及收集更多應用程式的資料。應用程式是由安全性研究人員、使用者和其他我們透過檢索網際網路及檢查其他市場安裝的應用程式而回報。
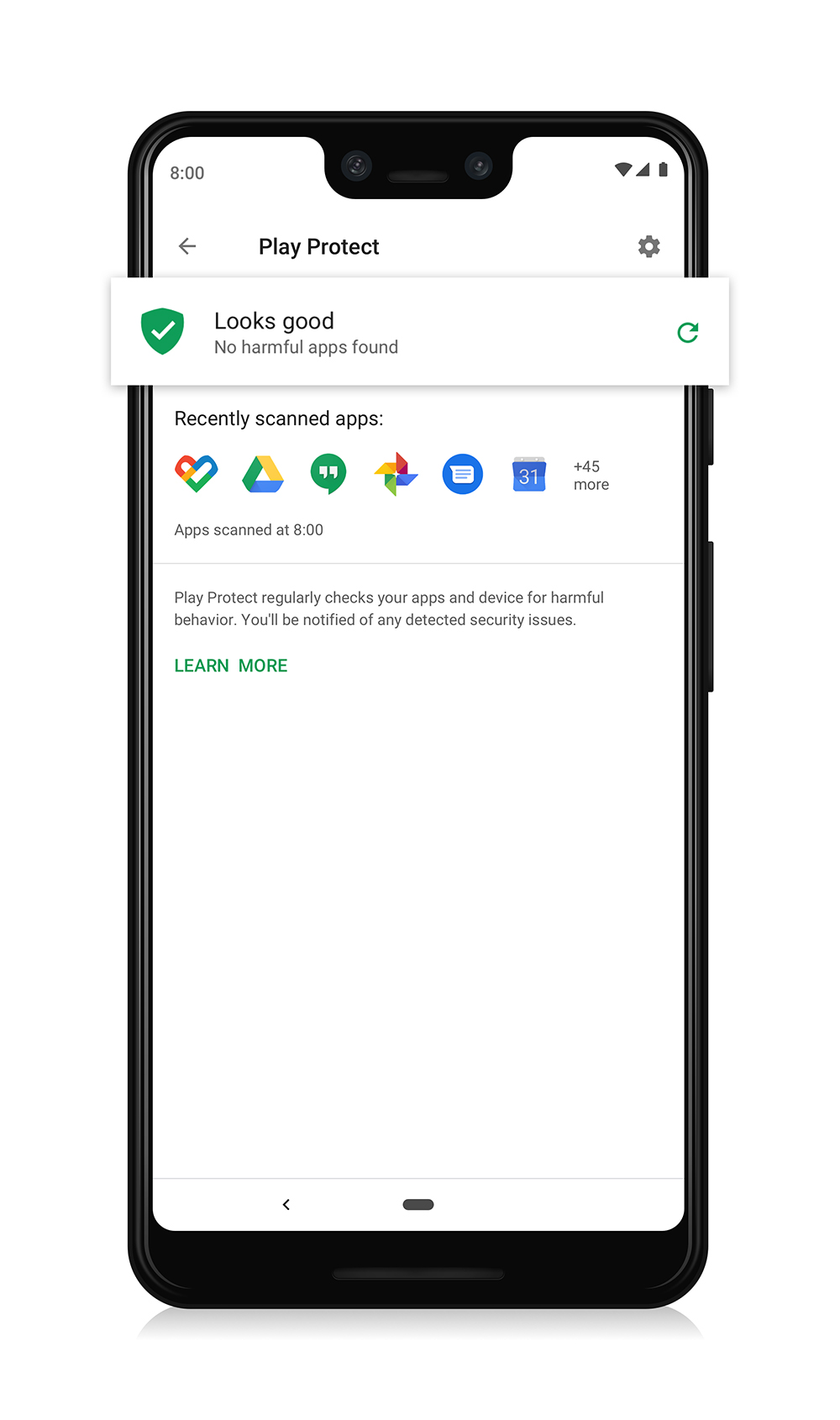
使用者只要在裝置上啟用 Google Play 安全防護中的「改善有害應用程式偵測效能」功能,即可允許 Google 審查新的應用程式。啟用這項功能可協助 Google 分析更多應用程式,以及系統分析的應用程式越多,Google Play 安全防護功能更能有效識別及限制對所有裝置對 PHA 的影響。
機器學習
Play 安全防護運用 Google 強大的機器學習演算法打擊 PHA。Google 系統會分析整個應用程式資料庫,瞭解哪些應用程式有害,哪些則安全。演算法會檢視數百種信號,並比較 Android 生態系統中的行為,看看是否有任何應用程式出現可疑行為,例如以非預期的方式與裝置上的其他應用程式互動、在未經授權的情況下存取或分享個人資料、主動安裝應用程式 (包括 PHA)、存取惡意網站,或略過內建的安全性功能。這些演算法也有助我們瞭解 PHA 的來源和營利方式,以便判斷這類應用程式背後的動機。
我們會使用以下工具,訓練機器辨識良好和不良行為。
 靜態分析
靜態分析系統會分析應用程式的程式碼,然後擷取這些功能,並與預期的良好行為和潛在不良行為進行比較。
 第三方報表
第三方報表GPP 促進與產業安全研究人員的積極關係。這些研究人員會以各種方式評估應用程式,並提供意見回饋,協助我們改善應用程式。
 簽名
簽名GPP 會使用簽章來比較應用程式與已知的有害應用程式和安全漏洞資料庫。
 開發人員關係
開發人員關係GPP 會分析非程式碼功能,判斷應用程式之間的可能關係,並評估建立應用程式的開發人員是否與建立 PHA 相關聯。
 動態分析
動態分析GPP 會執行應用程式,找出靜態分析無法呈現的互動行為。讓審查人員能找出需要存取伺服器和動態程式碼的攻擊。
 經驗法則與相似度分析
經驗法則與相似度分析GPP 會將應用程式進行比較,找出可識別有害應用程式的趨勢。
 SafetyNet
SafetyNetSafetyNet 是一種隱私權保護感應器網路,範圍涵蓋 Android 生態系統,並識別可能危害裝置的應用程式和其他威脅。
應用程式分類
GPP 分析應用程式後,會針對有害應用程式進行大規模的有害分類。標示為安全的應用程式和應用程式更新會在 Google Play 中提供。如果應用程式標示為有害,就會遭到封鎖。如果審查演算法不清楚應用程式是否安全或有害,就會標示為可能有害。
Android 安全性團隊成員手動審查 PHA。蓄意進行惡意操作的開發人員將遭到停權,因此無法再於 Google Play 發布應用程式。
持續保護措施
即使使用者是從 Google Play 以外的來源下載應用程式,GPP 仍會繼續保護使用者。GPP 裝置端保護措施會掃描及分析裝置上的每個應用程式。
瞭解詳情
這個頁面中的內容和程式碼範例均受《內容授權》中的授權所規範。Java 與 OpenJDK 是 Oracle 和/或其關係企業的商標或註冊商標。
上次更新時間:2025-07-26 (世界標準時間)。
[null,null,["上次更新時間:2025-07-26 (世界標準時間)。"],[[["\u003cp\u003eGoogle Play employs automated and manual reviews to ensure app safety before and after they are available for download.\u003c/p\u003e\n"],["\u003cp\u003eGoogle Play Protect utilizes machine learning to identify and mitigate harmful apps by analyzing app behavior and comparing it against known threats.\u003c/p\u003e\n"],["\u003cp\u003eDevelopers are subject to review and must adhere to the Google Play Developer Distribution Agreement to publish apps.\u003c/p\u003e\n"],["\u003cp\u003eGoogle Play Protect safeguards users by continuously scanning installed apps, regardless of their source, for potentially harmful behavior.\u003c/p\u003e\n"],["\u003cp\u003eGoogle encourages users to enable "Improve harmful app detection" to enhance the system's ability to identify and protect against threats.\u003c/p\u003e\n"]]],["Google Play uses automated mechanisms and human analysts to review apps and developers before they are available for download. This includes developer account analysis, internal app review with static and dynamic methods, and data collection from various sources. Machine learning algorithms, leveraging tools like static and dynamic analysis, third-party reports, signatures, developer relationships, and SafetyNet, identify potentially harmful apps. Analyzed apps are classified and either approved or blocked. This ongoing protection extends to apps installed from outside Google Play.\n"],null,["# Cloud-based protections\n\nAnalysis and review\n-------------------\n\nBefore an app becomes available for download in Google Play we analyze and\nreview the app and its developers. Using automated detection mechanisms (for\nexample, machine learning) and human analysts, we make every effort to ensure\nthe apps that appear in Google Play aren't harmful to users or their\ndevices.\n\n### Developer review\n\nAs a developer, you must agree to the Google Play [Developer\nDistribution Agreement](https://play.google.com/about/developer-distribution-agreement.html) before you can submit your apps to Google Play.\nThis contract is a guide to the behavior we expect of developers who publish\napps in Google Play.\n\nAdditionally, Google Play uses a variety of methods to check that developers\nare complying with these policies. Google Play's internal risk engine analyzes\ninformation from a developer's Google account, actions, history, billing\ndetails, device information, and more.\nIf something suspicious turns up, we manually review the transactions to\nensure that the developer is compliant.\n\n### Internal app review\n\nApplications undergo a review process to confirm that they comply with Google\nPlay policies before they become available in Google Play. Google has developed\nan automated application risk analyzer that performs static and dynamic analysis\nof apps to detect Potentially Harmful Application (PHA) behavior. When Google's\napplication risk analyzer discovers something suspicious, it flags the app and\nrefers it to a security analyst for manual review.\n\n### App review outside of Google Play\n\nBecause we try to protect users from PHAs and mobile unwanted software (MUwS)\nregardless of the source, it's important that our systems analyze and collect\ndata on as many apps as possible. Apps are reported by security researchers, users, and others\nwe find by crawling the internet and inspecting installed apps from other\nmarkets.\n\nUsers can allow Google to review new apps by enabling the *Improve harmful\napp detection* feature in Google Play Protect on their device. Enabling this\nfeature helps Google to analyze more apps and the more apps our systems analyze,\nthe better Google Play Protect is at identifying and limiting the impact of PHAs\nfor all devices.\n\nMachine learning\n----------------\n\nPlay Protect leverages Google's powerful machine learning algorithms to\ncombat PHAs. Google's systems learn which apps are harmful and which are safe by\nanalyzing our entire app database. The algorithms look at hundreds of signals\nand compare behavior across the Android ecosystem to see if any apps show\nsuspicious behavior, such as interacting with other apps on the device in\nunexpected ways, accessing or sharing personal data without authorization,\naggressively installing apps (including PHAs), accessing malicious websites, or\nbypassing built-in security features. These algorithms also help us understand\nwhere PHAs come from and how they make money, so we can determine the motivation\nbehind these types of apps.\n\nHere are some of the tools we use to teach machines to identify good and bad\nbehavior. \n**Static analysis**\n\nThe app's code is analyzed and the features are\nextracted and compared against expected good behavior and potential bad behavior. \n**Third-party reports**\n\nGPP cultivates active\nrelationships with industry and academic security researchers. These researchers\nevaluate apps in a variety of ways and send in feedback regarding their findings. \n**Signatures**\n\nGPP uses signatures to compare apps against a\ndatabase of known bad apps and vulnerabilities. \n**Developer relationships**\n\nGPP analyzes non-code features to\ndetermine possible relationships between applications and to evaluate\nwhether the developer that created the application has been associated\nwith the creation of PHAs. \n**Dynamic analysis**\n\nGPP runs applications to identify interactive\nbehavior that can't be seen with static analysis. This allows reviewers\nto identify attacks that require server access and dynamic code downloading. \n**Heuristic and similarity analysis**\n\nGPP compares applications\nto find trends that identify harmful apps. \n**SafetyNet**\n\nSafetyNet is a privacy preserving sensor\nnetwork that spans the Android ecosystem and identifies apps and\nother threats that can harm devices.\n\nClassifying apps\n----------------\n\nAfter analyzing the apps, GPP classifies them on a scale of safe to harmful.\nApps and app updates that are marked as safe are adopted into Google Play.\nApps that are marked as harmful are blocked. If the review algorithms are\nunclear whether an app is safe or harmful, it's marked as potentially harmful.\nAndroid Security Team members review PHAs manually. Developers who knowingly\nperform malicious actions are banned and can no longer publish apps on Google Play.\n\nOngoing protection\n------------------\n\nGPP continues protecting users after they've installed an app,\neven if the is app downloaded from outside of Google Play.\nGPP's on-device protections scan and analyze every app on the device.\n\n\n[Learn more](/android/play-protect/client-protections)"]]


 靜態分析
靜態分析 第三方報表
第三方報表 簽名
簽名 開發人員關係
開發人員關係 動態分析
動態分析 經驗法則與相似度分析
經驗法則與相似度分析 SafetyNet
SafetyNet
