分析和审核
在应用可供下载之前,我们会分析并审核应用及其开发者。借助自动检测机制(例如机器学习)和人工分析师,我们会尽一切努力确保 Google Play 中显示的应用对用户或其设备不有害。
开发者审核
作为开发者,您必须同意 Google Play 开发者分发协议,才能向 Google Play 提交应用。 此合同旨在指导我们在 Google Play 上发布应用的开发者应遵守的行为。
此外,Google Play 还会使用各种方法来检查开发者是否遵守这些政策。Google Play 的内部风险引擎会分析开发者 Google 帐号中的信息、操作、历史记录、结算明细、设备信息等。 如果发现可疑情况,我们会人工审核相应交易,以确保开发者遵守相关规定。
内部应用审核
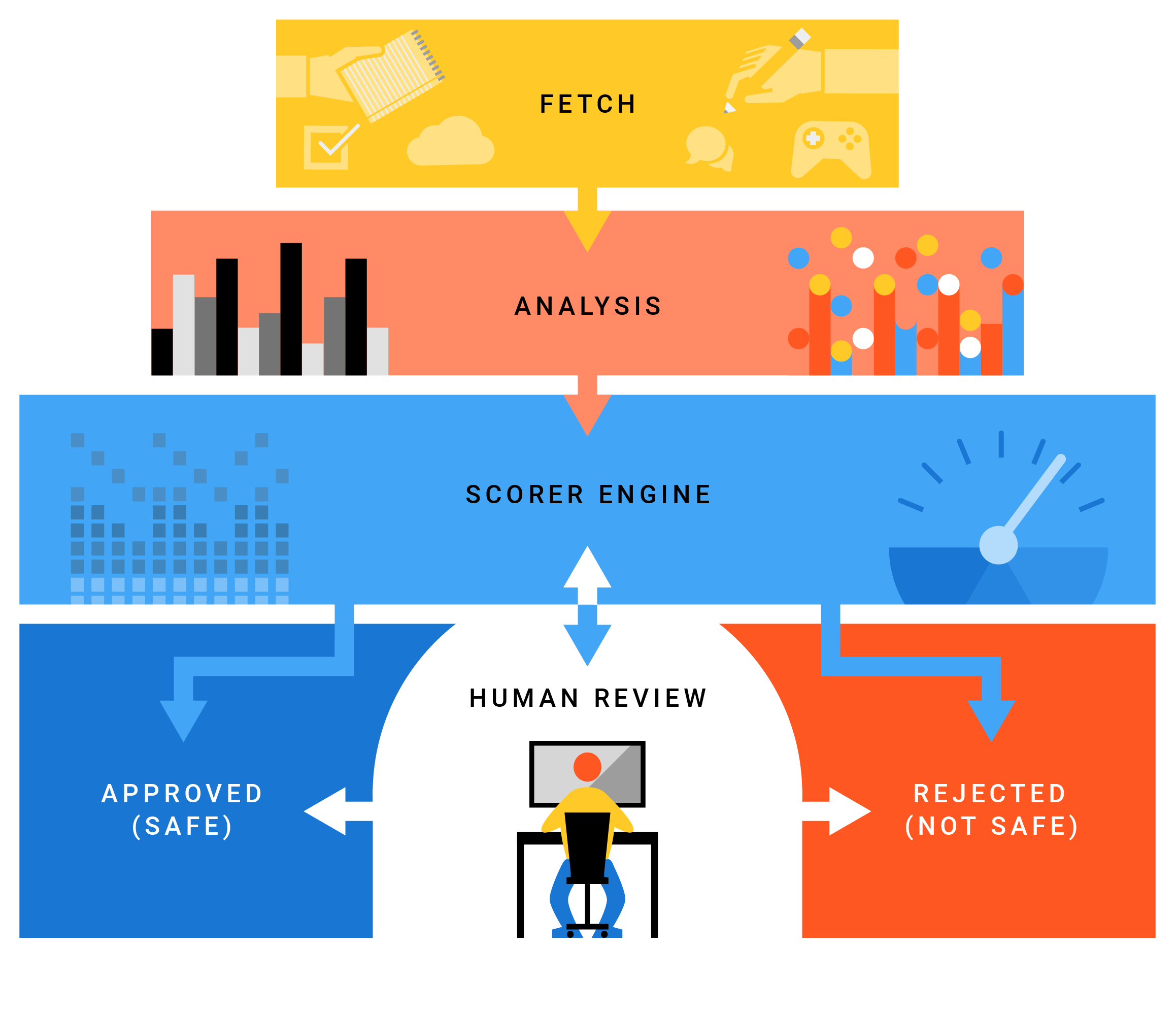
应用会进入审核流程,以确认其符合 Google Play 政策,然后才能在 Google Play 上架。Google 开发了一款自动化应用风险分析器,可对应用执行静态和动态分析,以检测潜在有害应用 (PHA) 行为。当 Google 的应用风险分析器发现可疑内容时,它会标记应用并将其交由安全分析师进行人工审核。
Google Play 之外的应用评价
无论来源是什么,我们都会尽力保护用户免受 PHA 和移动垃圾软件 (MUwS) 的侵扰,因此我们的系统必须分析尽可能多的应用并收集相关数据,这一点非常重要。应用是由安全研究人员、用户以及通过抓取互联网和检查来自其他市场的已安装应用找到的其他用户报告的。
用户可以在其设备上的 Google Play 保护机制中启用改进有害应用检测功能,以允许 Google 审核新应用。启用此功能有助于 Google 分析更多应用,我们的系统分析的应用越多,Google Play 保护机制在识别和限制 PHA 对所有设备的影响方面就越好。
机器学习
Play 保护机制利用 Google 强大的机器学习算法来防范 PHA。Google 的系统会通过分析整个应用数据库来了解哪些应用是有害的,哪些是安全的。这些算法会分析数百种信号并比较整个 Android 生态系统的行为,以了解是否有任何应用出现可疑行为,例如以意想不到的方式与设备上的其他应用交互、在未经授权的情况下访问或分享个人数据、恶意安装应用(包括 PHA)、访问恶意网站或绕过内置安全功能。这些算法还有助于我们了解 PHA 的来源及其创收方式,以便我们能够确定这类应用背后的动机。
以下是我们用来教机器识别良好和不良行为的一些工具。
 静态分析
静态分析系统会分析应用的代码,提取功能,并将其与预期的良好行为和潜在的不良行为进行比较。
 第三方报告
第三方报告GPP 与业界和学术安全研究人员培养积极的关系。这些研究人员通过各种方式评估应用,并发送关于其发现结果的反馈。
 签名
签名GPP 使用签名将应用与包含已知不良应用和漏洞的数据库进行比较。
 开发者关系
开发者关系GPP 会分析非代码功能,以确定应用之间可能存在的关系,并评估创建应用的开发者是否与 PHA 的创建相关联。
 动态分析
动态分析GPP 运行应用以识别静态分析无法检测到的互动行为。这样,审核人员就可以识别需要访问服务器和下载动态代码时的攻击。
 启发词语和相似度分析
启发词语和相似度分析GPP 会对应用进行比较,以找出识别有害应用的趋势。
 SafetyNet
SafetyNetSafetyNet 是一个可保护隐私的传感器网络,它覆盖 Android 生态系统,可识别可能危害设备的应用和其他威胁。
应用分类
对应用进行分析后,GPP 会按照“安全无害”的等级对应用进行分类。 标记为安全的应用和应用更新会采用 Google Play。 系统会屏蔽标记为有害的应用。如果审核算法不清楚应用是安全还是有害,就会被标记为“可能有害”。 Android 安全团队成员会人工审核 PHA。故意执行恶意操作的开发者将被禁止,并且无法再在 Google Play 上发布应用。

持续保护
在用户安装应用后,GPP 会继续保护用户,即使应用是从 Google Play 以外的地方下载的也不例外。 GPP 的设备端保护功能会扫描和分析设备上的每个应用。
